In my previous blog post I showed how to audit unwanted Azure resource configurations. Now, listing non-compliant resources is fine and can be a great help, but would it not be much better if we could just prevent unwanted configurations from being deployed?
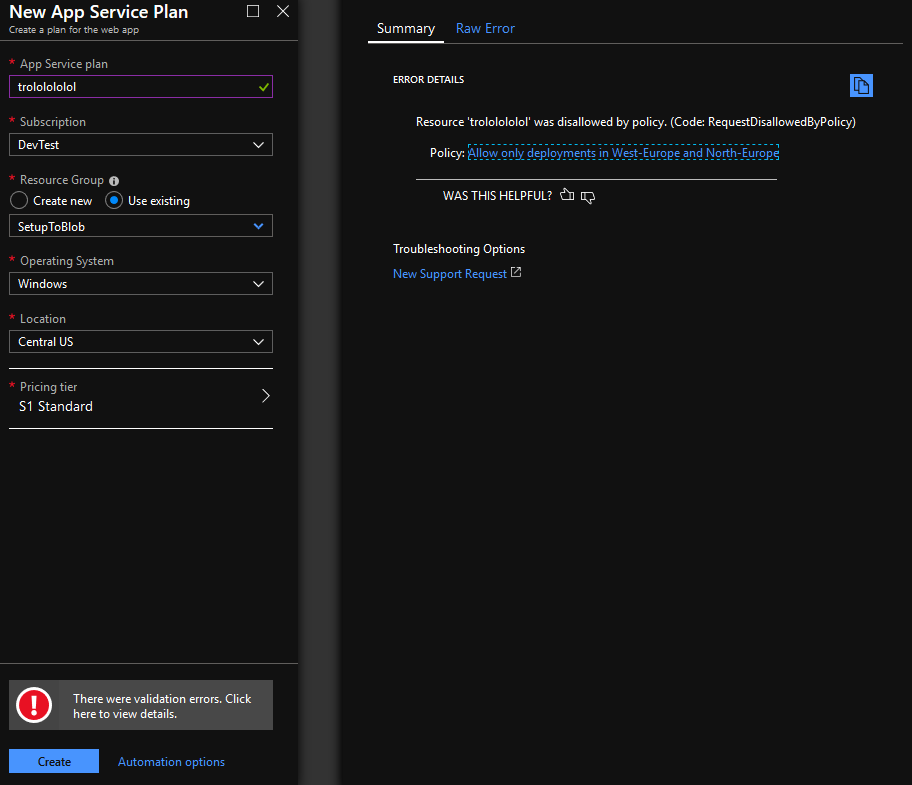
Deny any deployment not in Europe
Let’s take the example of Azure regions. If you are working for an organization that wants to operate just within Europe, it might be best to just deny any deployment outside of West- and North-Europe. This will help prevent mistakes and help enforce rules within the organization. How would we write such a policy?
Any policyRule still consist out of two parts, an if and an then. First, the if – which acts like a query on our subscription or resourcegroup and determines to which resources the policy will be applied. In this case we want to trigger our policy under the following condition: location != ‘North Europe’ && location != ‘West Europe.’ We write this using JSON, by nesting conditions. This syntax is a bit verbose, but easy to understand. The effect that we want to trigger is a simple deny of any deployment that matches this condition. In JSON, this would look like this:
{
"type": "Microsoft.Authorization/policyDefinitions",
"name": "audit-vms",
"properties": {
"displayName": "Audit every Virtul Machine",
"description": "This policy audits any virtual machine that exists in the assigned scope.",
"policyRule": {
"if": {
"allOf": [
{
"field": "location",
"notEquals": "westeurope"
},
{
"field": "location",
"notEquals": "northeurope"
}
]
},
"then": {
"effect": "deny"
}
}
}
}
Creating a policy like this and then applying it to an subscription or resourcegroup, will the Azure Resource Manager instruct to immediately deny any deployment that violates the policy. With the following as a result:
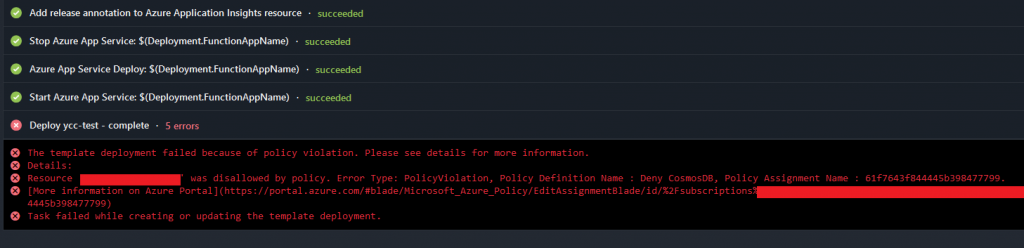
Azure Policy is also evaluated when deploying from Azure Pipelines, where you will also get a meaningfull error when trying to deploy any template that violates a deny policy:
1 reactie